People and Procedures
Key Areas
Apply cyber security measures at every level!
Your internal processes and your workforce are the last, and one of the most important lines of defence
Address how you can manage who can access and control your business’ information
Train your staff

Passphrases
What?
Using a phrase or sentence, not one word, as your password
A passphrase is similar to a password. It is used to verify access to a computer system, program or service. Passphrases are most effective when they are:
- Used with multi-factor authentication
- Unique – not a famous phrase or lyric, and not re-used
- Longer – phrases are generally longer than words
- Complex – naturally occurring in a sentence with uppercase, symbols and punctuation
- Easy to remember – saves you being locked out.
Why?
Greater security & more convenience
- Harder to crack against common password attacks
- Easier to remember than random characters
- Meets password requirements easily – upper and lower-case lettering, symbols and punctuation
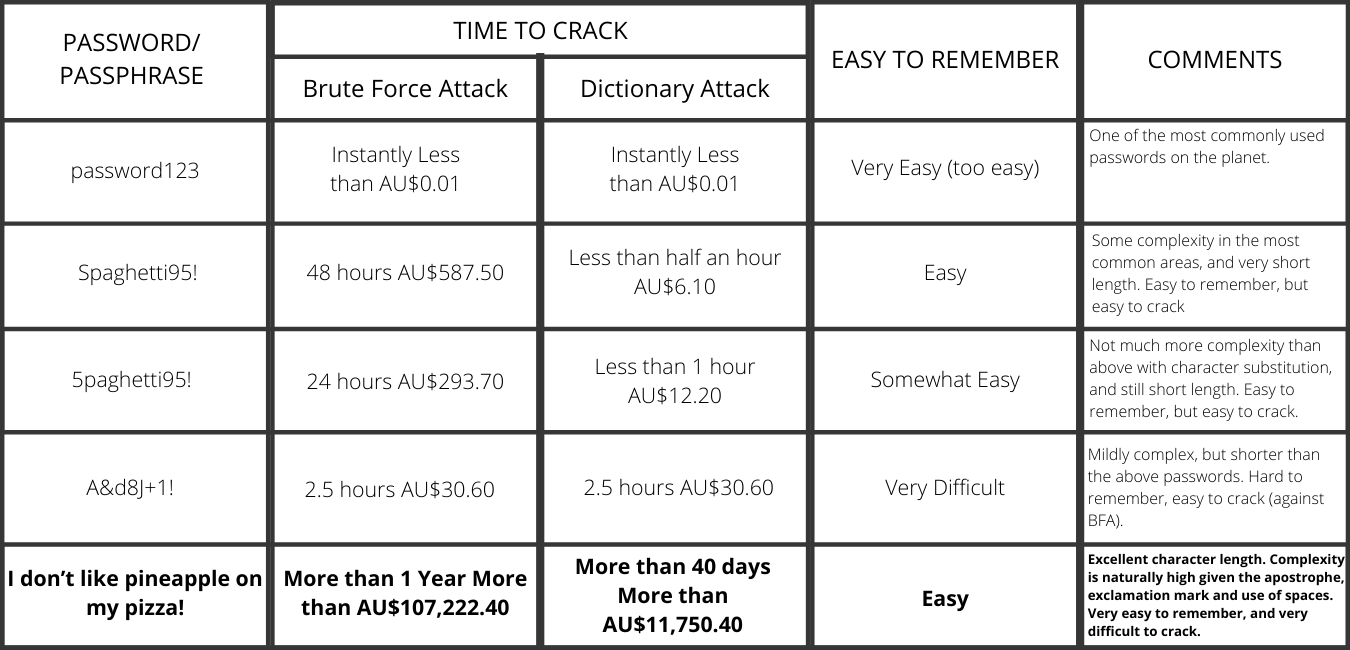
Brute Force Attacks and Dictionary Attacks
both generate millions of password/passphrase attempts per second.
Where?
For all fixed and mobile devices
Passphrases will significantly increase security across all of your business’ devices. See below for a comparison of password vs passphrase security.
Access Control
What?
A process to regulate who can access what within your business’ computing environment
Access control is a way to limit access to a computing system. It allows business owners to:
- Decide who they would like to give access privileges to
- Determine which roles require what access
- Enforce staff access control limits.
Why?
To minimise risk of unauthorised access to important information
Many small businesses employ internal staff or outsource work to external suppliers e.g. website hosting companies.
Access control systems help you protect your business by allowing you to limit staff and supplier access to your computer:
- Networks
- Files
- Applications
- Sensitive data
Who?
Principle of least privilege
Depending on the nature of your business, the principle of least privilege is the safest approach for most small businesses. It gives users the bare minimum permissions they need to perform their work. This also reduces the risk of an ‘insider’ accidentally or maliciously endangering your business.
Employee Training
What?
Education to protect your staff and business against cyber threats
A cyber security incident response plan can help to change the habits and behaviours of staff and create a sense of shared accountability in keeping your small business safe. Your cyber security incident response plan teaches staff how to:
- Recognise
- Avoid
- Report
- Remove
- Recover
Why?
Employees can be the first and last line of defence against cyber threats
Employees make mistakes. As business owners, you have a legal responsibility to keep your business and customer information safe. That’s why having a cyber security training program is vital.
When?
Regular cyber security awareness and training
Cyber security is continuously evolving. Keeping everybody up to date could be the difference between whether or not a criminal accesses your money or data.

Learning about cyber security for the fist time?
Or are you keeping yourself up to date? This guide is an excellent place to start! If you want to improve your cyber security further, you can find more information and advice on the ACSC website at: www.cyber.gov.au.
The ACSC is here to help make Australia the safest place to connect online.
The Australian Cyber Security Centre (ACSC), as part of the Australian Signals Directorate (ASD), provides cyber security advice, assistance and operational responses to prevent, detect and remediate cyber threats to Australia.
